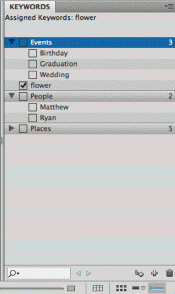
 How do you open the panel in the accompanying image?
How do you open the panel in the accompanying image?
A. Click Window on the Menu bar, then click the name of the panel.
B. Click View on the Menu bar, then click the name of the panel.
C. Click the Keywords button on the Favorites panel.
D. Click the Keywords button on the Metadata panel.
Answer: A
You might also like to view...
The security controls specified in ____________ can be shaped into a well-defined architecture of explicit security practices for a particular situation.
Fill in the blank(s) with the appropriate word(s).
Case-Based Critical Thinking QuestionsCase 2-2Life Decisions Cyber Cafe is a cafe with free Internet service and computers that are linked to various online career opportunities. They have set up their computers to display their Web site to help users have a starting point. The owner wants to add his e-mail address as a link so customers can send questions to him directly. What should he be most concerned with when designing the links?
A. e-mail address B. potential clients C. mailto tag D. potential spam
What is the effect of the following program segment?
assume the following environment ``` #define MAX 50 int a[MAX], i, j, temp; ``` ``` for (i = 0; i < MAX - 1; ++i) if (a[i] > a[i + 1]) { temp = a[i]; a[i] = a[i + 1]; a[i + 1] = temp; } ``` a. Arranges the elements of array a in ascending order. b. Counts the number of elements of a greater than its first element. c. Reverses the numbers stored in the array. d. Puts the largest value in the last array position. e. None of the above.
Ink jet printers only print in black and white.
Answer the following statement true (T) or false (F)