In the ________ model, the user has control over the applications but has limited or no control over the underlying infrastructure
A) SaaS
B) IaaS
C) PaaS
D) data
C
You might also like to view...
Is a DFD an effective documentation technique for identifying who or what performs a particular task? Explain
Which of the following statements about the interaction of Friedman’s philosophy and ISO 26000 is accurate?
a. Friedman would support most of the ISO 26000 recommendations even if they didn’t help raise profits. b. There are no inherent conflicts between what Friedman argued and what ISO 26000 is trying to accomplish. c. Friedman would oppose the creation of the ISO 26000 recommendations. d. Friedman would oppose adoption of many ISO 26000 recommendations.
What formula will correctly calculate the expected NPV in C5?
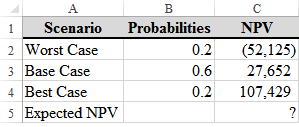
a) {=SUM(B2:B4*C2:C4)}
b) =SUM(B2:B4)*SUM(C2:C4)
c) =SUMPRODUCT(B2:B4,C2:C4)
d) A and B
e) A and C
A common major disadvantage of secondary data is the _____
a. unsuitable units of measurement b. long time period required to collect data c. high cost for data collection d. known source and control over data collection