An attack that changes a symlink on a Linux system between the time that an account's rights to the file are verified and the file is accessed is an example of what type of attack?
A. Unlinking
B. Tick/tock
C. setuid
D. TOCTOU
Answer: D. TOCTOU
Computer Science & Information Technology
You might also like to view...
When is the incident reporting function set in motion?
What will be an ideal response?
Computer Science & Information Technology
Outline view displays the text of your slides instead of slide ____________________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Which of the following is not one of the four anomalies that may occur when creating database tables?
A) data redundancy B) update anomaly C) primary anomaly D) insert anomaly E) deletion anomaly
Computer Science & Information Technology
Case 1Alex inherits an existing project from a co-worker. He familiarizes himself with the contents of the figure shown below.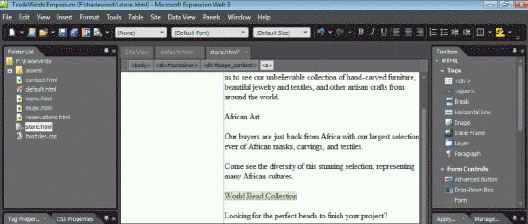 What does the dashed line under the words "World Bead Collection" indicate?
What does the dashed line under the words "World Bead Collection" indicate?
A. hyperlink B. graphic C. error D. bookmark
Computer Science & Information Technology