Which of the following can be used to detect system breaches and alert a system administrator?
a. IDS
b. Firewall
c. NAT
d. Proxy
ANS: A
You might also like to view...
The sqrt function
a) is provided in the
What type of memory module is most likely found in systems with space restrictions and requires a smaller alternative to a DIMM?
a. RDRAM b. SODIMM c. SIPP d. SIMM
PowerPoint takes less time to insert embedded and linked objects than it takes to perform an ordinary cut-and-paste or copy-and-paste action.
Answer the following statement true (T) or false (F)
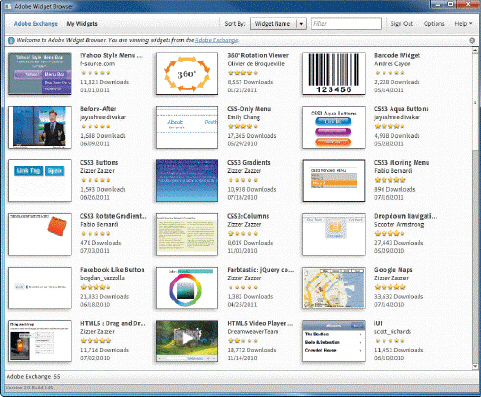 The items shown in the accompanying figure are parts of a(n) ___________ User Interface that enable users to interact with the application and operating system.
The items shown in the accompanying figure are parts of a(n) ___________ User Interface that enable users to interact with the application and operating system.
Fill in the blank(s) with the appropriate word(s).