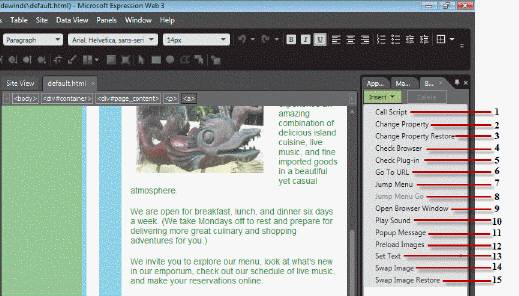
 Referring to the figure above, the behavior labeled ____ is useful for customizing pages to specific browsers.
Referring to the figure above, the behavior labeled ____ is useful for customizing pages to specific browsers.
A. 2
B. 4
C. 5
D. 13
Answer: B
You might also like to view...
Answer the following statements true (T) or false (F)
1. A method’s changes to a variable that is passed by value do not affect the value of the original variable. 2. Keyword Val is used to pass an argument by value. 3. Passing arguments by reference can weaken security because the called method can modify the caller’s data.
In general, the overhead incurred by ________ allocation is outweighed by the advantages of being able to store more processes in main memory at the same time.
a) contiguous b) noncontiguous c) fragment d) segment
In the Windows operating systems, deleting a file from the Recyle Bin performs which of the following actions on the data stored on the surface of the medium?
a. Nothing happens to the data at this point. It is simply moved from the original folder to a hidden folder in the Recycle Bin. b. Nothing happens to the data at this point. The allocation marker for the file is simply reset. c. A random deluge of zeroes and ones is copied over the original data. d. The entry for the file is purged from the $MFT metadata file in the file system.
Security code scanners also report a number of false positives.
Answer the following statement true (T) or false (F)