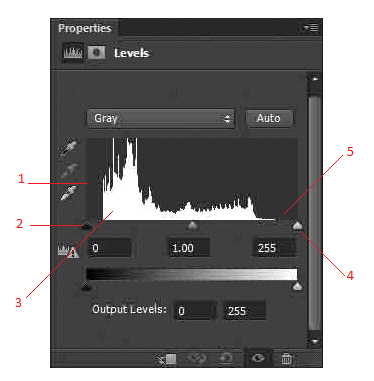
 In the accompanying figure, item 4 points to the ____.
In the accompanying figure, item 4 points to the ____.
A. white point
B. black point
C. histogram
D. grayscale point
Answer: A
You might also like to view...
In a salami-slicing attack, a program performs a large number of small, hardly noticeable malicious actions, which add up to a large aggregate malicious action. In a classic example, a programmer for a bank has 1 cent of the monthly interest calculation on each bank customer's account transfered into his account. Thus, if the bank has 1,000,000 customers, then this programmer would get $10,000
each month from this salami slicing attack. What type of malware is such a program? What will be an ideal response?
If the ipv6 ospf hello-interval 5 Cisco IOS command is entered on an Ethernet interface, what would the OSPFv3 dead interval be set to?
A) 30 B) 40 C) 15 D) 20
Which of the following is a feature of fault tolerance control?
A. interruptible power supplies B. RAID C. DDP D. MDP
Name the four audio sources that Unity supports.
What will be an ideal response?