Which of the following specifies the authorization level that each user of an information asset is permitted to access, subject to the need-to-know principle?
A. discretionary access controls
B. task-based access controls
C. security clearances
D. sensitivity levels
Answer: C
Computer Science & Information Technology
You might also like to view...
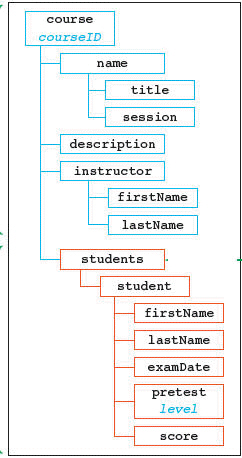 In the accompanying figure, name is an element from the _______ vocabulary.
In the accompanying figure, name is an element from the _______ vocabulary.
A. students B. instructor C. course D. description
Computer Science & Information Technology
Quick Storage _____________ can move the virtual disks of a running machine regardless of the storage type.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
A useful CLI to copy and convert data, such as for benchmarking purposes, is
A) c B) cd C) cp D) dd
Computer Science & Information Technology
In a ____, the tree is structured as a shallow hierarchy where there is no subordinate CAs.
A. web of trust B. Web hierarchy C. distributed model D. trusted issuer hierarchy
Computer Science & Information Technology