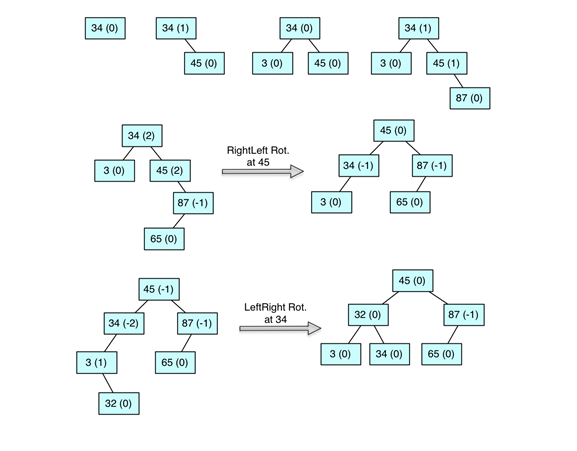
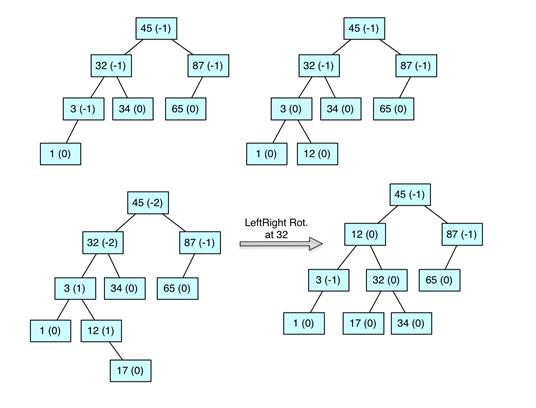
this time assuming an AVL tree. Include the balance factors in your drawing.
What will be an ideal response?
You might also like to view...
It is often argued that peer-to-peer systems can offer anonymity for
(i) clients accessing resources (ii) the hosts providing access to resources. Discuss each of these propositions. Suggest a way in which the resistance to attacks on anonymity might be improved.
A form can be used to make users view or edit only one record at a time
Indicate whether the statement is true or false
What do you do as a technician if an Internet search has no relevant links on the first page?
A) Try the same search in a different search engine. B) Reboot the computer. C) Try different search terms. D) Add quotation marks before the first term and after the last term.
You run a website in an IaaS environment. You wake up to discover that your website has been defaced. Assume you are running a web server and an FTP server in this environment and that both an application proxy and a firewall sit between those servers and the Internet. All of your VMs are running SSH servers. What logs might help you determine how the website was defaced? What kind of information
would you look for? What will be an ideal response?