Enumerable static method ________ creates a list of elements containing the first argument’s value. The length of the list is specified by the second argument.
a) Enumerate
b) Repeat
c) Generate
d) None of the above.
b) Repeat
You might also like to view...
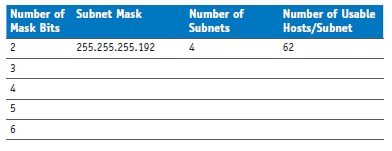
Complete the following table, given Class C subnetting.
Match the following fields with the information they provide
I. Title A. current hour, minute, and second II. Subject B. current month, day, and year III. Author C. a blank field where the user may enter the Title of the document IV. Time D. a blank field where the user may enter the Subject of the document V. Date E. username provided when the software was registered
The reconnaissance phase of an attack occurs from outside of the network.
Answer the following statement true (T) or false (F)
________ is the result of someone's creativity and knowledge and usually is protected by copyrights.
What will be an ideal response?