What scenario describes an evil twin attack?
a. A malicious access point is configured with the SSID of a non-malicious public access point.
b. An attacker is actively attempting to brute force the PIN of a WPS enabled access point.
c. A hacker is actively sending wireless probes to discover available wireless networks.
d. A hacker is utilizing a protocol analyzer on a public Wi-Fi network to discover packet contents.
ANSWER: a
You might also like to view...
The number of calls to recursively calculate the Fibonacci value of 7 is:
a. 7 b. 13 c. 41 d. 39
The Utility menu included with many inkjet printers provides a variety of diagnostic tools. The ______ utility is used to correct misaligned vertical straight-line or large characters
a. Status or ink monitor b. Nozzle check c. Head cleaning d. Print head alignment
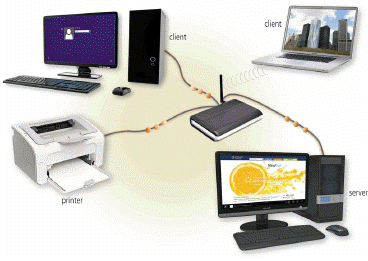
A. resources B. systems C. links D. media
This process improves system performance by acting as a temporary high-speed holding area between a secondary storage device and the CPU.
A. RAID B. data access C. data compression D. disk caching