Include your answer on the convergence time from Step4.
What will be an ideal response?
The result of ping 10.0.1.10 command is like the following:
```
PING 10.0.1.10 (10.0.1.10) 56(84) bytes of data.
64 bytes from 10.0.1.10: icmp_seq=2 ttl=62 time=5.18 ms
64 bytes from 10.0.1.10: icmp_seq=3 ttl=62 time=1.25 ms
. . . . . . .
64 bytes from 10.0.1.10: icmp_seq=20 ttl=62 time=1.26 ms
64 bytes from 10.0.1.10: icmp_seq=21 ttl=62 time=1.26 ms
ethereal-capture: Symbol `pcap_version' has different size in shared object, con
sider re-linking
From 10.0.4.10 icmp_seq=100 Destination Host Unreachable
From 10.0.4.10 icmp_seq=101 Destination Host Unreachable
From 10.0.4.10 icmp_seq=102 Destination Host Unreachable
. . . . . . . .
From 10.0.4.10 icmp_seq=194 Destination Host Unreachable
From 10.0.4.10 icmp_seq=195 Destination Host Unreachable
ping: sendmsg: Network is unreachable
From 10.0.4.10 icmp_seq=196 Destination Host Unreachable
From 10.0.4.10 icmp_seq=197 Destination Host Unreachable
ping: sendmsg: Network is unreachable
ping: sendmsg: Network is unreachable
64 bytes from 10.0.1.10: icmp_seq=219 ttl=61 time=6.40 ms
64 bytes from 10.0.1.10: icmp_seq=220 ttl=61 time=1.68 ms
64 bytes from 10.0.1.10: icmp_seq=221 ttl=61 time=1.73 ms
64 bytes from 10.0.1.10: icmp_seq=222 ttl=61 time=1.68 ms
--- 10.0.1.10 ping statistics ---
222 packets transmitted, 24 received, +98 errors, 89% packet loss, time 221243ms
rtt min/avg/max/mdev = 1.251/1.697/6.403/1.255 ms, pipe 3
``` After ICMP sequence number 21 with the response time of 1.26 ms, the network hangs and PC1 receives the response of ICMP sequence number 219 with 6.40 ms. Ping command issues ICMP request every second. Therefore the total duration is (219 s + 6.40 ms) – (21 s + 1.26 ms). So it takes around 198 seconds.
You might also like to view...
What information does the BSIMM publish regarding scorecards from participating organizations?
Fill in the blank(s) with the appropriate word(s).
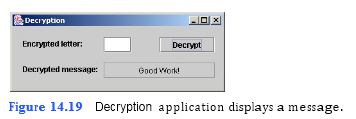
Develop an application that allows a user to decrypt a secret message (a string of numbers). The user should enter each number of the message one at a time in a JTextField. When the Decrypt JButton is clicked, the number should be decrypted to a letter. That letter should then be appended to the Decrypted message: JTextField. When the user enters the numbers 39, 79, 79, 68, 0, 55, 79, 82, 75, 1 in order, your application should appear as in Fig. 14.19.
a) Copying the template to your working directory. Copy the C:Exam- plesTutorial14ExercisesDecryption directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the Decryption.java file in your text editor.
c) Adding an instance variable. After the last GUI component is declared (line 18), add a declaration for a private String named message which will hold the decrypted message. Initialize message to the empty string. Use one line for a com- ment.
d) Storing the user input. Add code in the decryptJButtonActionPerformed method that will store the user input in an int variable named encryptedLetter. The rest of the code you will add in this exercises should be placed in the decryptJButtonAc- tionPerformed method.
e) Testing the user input. Your application should only accept user input in the range 0 to 94. Add an if statement that will test whether the user’s input is in the accepted range of values.
f) Decrypting the input. Add
Which of the following is a type of corner available in the Corner Options dialog box?
A. Select B. Acute C. Beveled D. Baseline
What should the forensics specialist keep updated and complete in order to support his or her role as an expert and document enhancement of skills through training, teaching, and experience?
a. His or her testimony b. His or her CV c. The examination plan d. The deposition