Range names must begin with _____.
A. a letter or an underscore
B. a number
C. a hash tag
D. an asterisk
Answer: A
You might also like to view...
Given the following class definition, how would you declare an object of the class, so that the object automatically called the default constructor?
class ItemClass { public: ItemClass(); ItemClass(int newSize, float newCost); int getSize(); float getCost(); void setSize(int newSize); void setCost(float newCost); private: int size; float cost; }; a. ItemClass() myItem; b. ItemClass myItem(1, 0.0); c. ItemClass myItem; d. ItemClass myItem(); e. You can not do this
The compression function used in secure hash algorithms falls into one of two categories: a function specifically designed for the hash function or an algorithm based on a ___________ .
Fill in the blank(s) with the appropriate word(s).
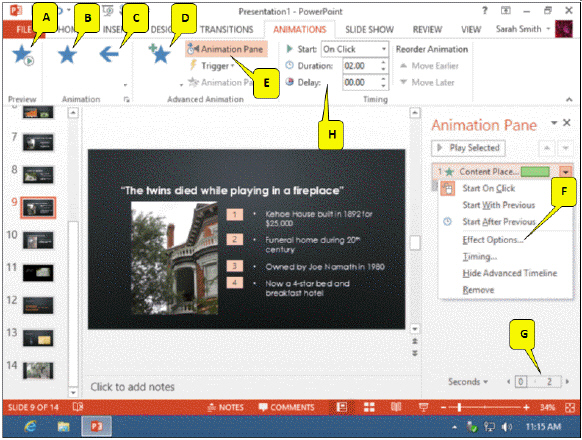 Referring to the figure above, which callout points to the Add Animation button to select an animation effect?
Referring to the figure above, which callout points to the Add Animation button to select an animation effect?
A. A B. B C. C D. D
Create an applet that draws a pattern of circles whose centers are evenly spaced along a horizontal line. Use six constants to control the pattern: the number of circles to draw, the diameter of the first circle, the x- and y-coordinates of the center of the first circle, the distance between adjacent centers, and the change in the diameter of each subsequent circle.
What will be an ideal response?