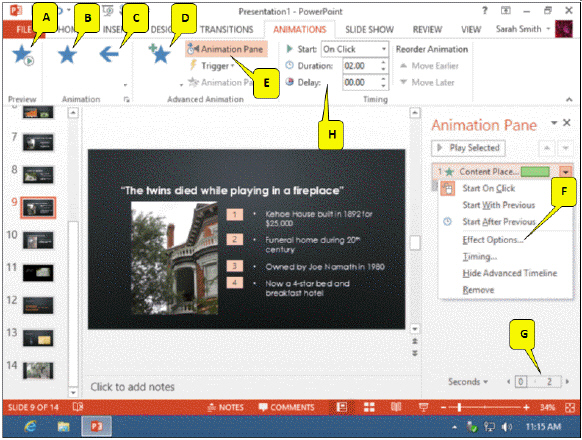
 Referring to the figure above, which callout points to the option used to add sound to an animation?
Referring to the figure above, which callout points to the option used to add sound to an animation?
A. E
B. F
C. G
D. H
Answer: B
You might also like to view...
________ intrusion-detection software monitors traffic on a network for any unusual patterns that might indicate DoS attacks or attempted entry into a network by an unauthorized user.
a) Host-based. b) Firewall-based. c) Network-based. d) None of the above
Which presentation software view hides the toolbars, ribbons, and other controls used to create the presentation and displays each slide at the full size of the screen?
A. Design B. Review C. Animations D. Slide Show
An ordered list
a. Bulleted list b. Numbered list c. Sequential list
Which of the following is a threat to a VoIP network?
a. Call flooding. b. Information is accessed by unauthorized persons. c. Attacker becoming a trusted member of the network. d. All the above are threats.