Many certificates conform to the ____ standard.?
A. ?X.309
B. ?X.409
C. ?X.509
D. ?X.609
Answer: C
Computer Science & Information Technology
You might also like to view...
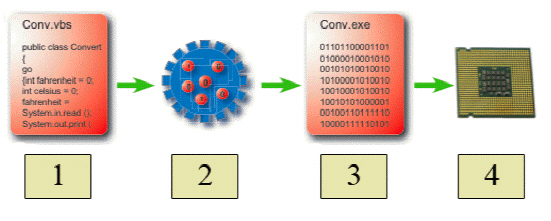 In the accompanying figure, item 2 represents a(n) ____.
In the accompanying figure, item 2 represents a(n) ____.
A. variable B. compiler C. algorithm D. interpreter
Computer Science & Information Technology
All wireless networks have their own name, referred to as the ________, which is used to identify the network
Fill in the blank(s) with correct word
Computer Science & Information Technology
List three main ways in which presentations of output are unintentionally biased.
What will be an ideal response?
Computer Science & Information Technology
Ticket-Granting-Tickets (TGTs) are common in which of the following authentication schemes?
A. LDAP B. RADIUS C. Kerberos D. TACACS+
Computer Science & Information Technology