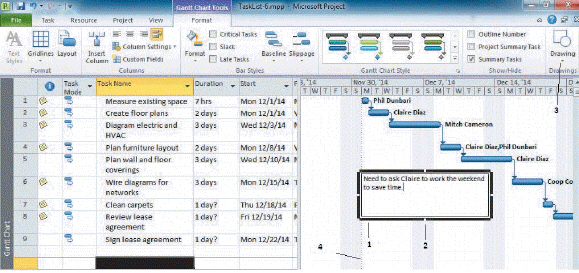
 The small white rectangle marked 2 in the accompanying figure is called a ____ handle.
The small white rectangle marked 2 in the accompanying figure is called a ____ handle.
A. embedded
B. text
C. modification
D. sizing
Answer: D
Computer Science & Information Technology
You might also like to view...
A(n) __________ represents a storage location in the computer's memory.
a. literal b. variable c. comment d. integer e. None of these
Computer Science & Information Technology
A fundamental tool for intrusion detection is the _________ record. ?
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The ____ metacharacter is used to allow a string to contain an alternate set of substrings.
A. (!) B. (|) C. (\) D. (/)
Computer Science & Information Technology
When a GPO is linked to a site object, what will be affected?
A. All users and computers physically located at the site B. All users physically located at the site C. All computers physically located at the site D. Any computers or users connected logically to the site
Computer Science & Information Technology