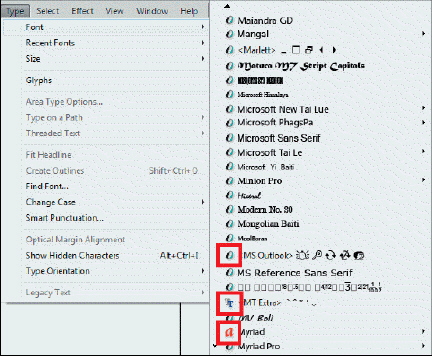
 The icon in the top red box of the accompanying figure indicates that the font is ______________.
The icon in the top red box of the accompanying figure indicates that the font is ______________.
Fill in the blank(s) with the appropriate word(s).
Open Type
Computer Science & Information Technology
You might also like to view...
The statement, “All financial transactions are to be encrypted using 3DES” is an example of a:
a. Procedure b. Guideline c. Standard d. Policy
Computer Science & Information Technology
As part of DirectAccess configuration, which of the following is also configured?
A. Remote Desktop Server B. Virtual Private Network Server C. Network Location Server D. Remote Assistance Server
Computer Science & Information Technology
Cough preparations containing less than 200 milligrams of codeine per 100 milliliters or grams fall into Schedule _____
a. II b. III c. IV d. None of the above
Computer Science & Information Technology
____ cryptography enables exchange of secure messages between parties without prior arrangement to exchange keys.
A. Public key B. Secret key C. Symmetric D. Private key
Computer Science & Information Technology