You can download the OneDrive app on your Windows Phone or Android but not for your iPhone, or iPad
Indicate whether the statement is true or false
FALSE
You might also like to view...
A Trojan can do which of the following?
A) Delete files B) Open a backdoor on the infected system C) Install a key logger or other spyware on the infected system D) All of the above
From the XML document in Fig. 11.15, answer the following questions.
Fig, 11.15
```
1
23
Create one or more of the following suites for the protocol:
Using the three-tier software architecture presented in this chapter, design and implement a client-server suite for the following protocol (it is not a well-known service): Each client sends to the server a name. The server accumulates the names received from successive clients (by appending each, with a linefeed (‘
’), to a static string). Upon receiving a name, the server sends the names that it has collected to the client. The figure below illustrates the sequence diagram of a session of the protocol.
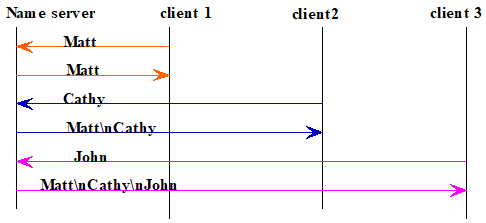
i.
Connectionless server;
A(n) ________ is a note or comment placed at the conclusion of a section or a document
Fill in the blank(s) with correct word