A(n) ________ can protect you from both incoming and outgoing Internet traffic
Fill in the blank(s) with correct word
firewall
You might also like to view...
Answer the following statements true (T) or false (F)
1. An algorithm is a step-by-step sequence of instructions for carrying out some task. 2. A sequence of instructions for assembling a bookcase does not qualify as an “algorithm” since the instructions are not written in formal, mathematical notation. 3. For a precise, clearly-stated problem, there can be only one algorithm that solves that problem. 4. Big-Oh notation is used to measure the exact number of seconds required by a particular algorithm when executing on a particular computer. 5. Suppose you have been given a sorted list of 100 names and need to find a particular name in that list. Using sequential search, it is possible that you might have to look at every location in the list before finding the desired name.
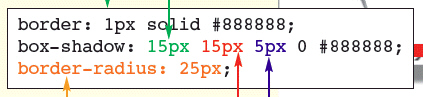 As shown in the accompanying figure, a positive h-shadow value pushes the shadow ____.
As shown in the accompanying figure, a positive h-shadow value pushes the shadow ____.
A. to the left B. up C. down D. to the right
Which of the following is not a way to address data validation violations?
A) Correct the data. B) Press the "Allow This Exception" button and keep going. C) Change the data validation rule. D) Cancel the record entry.
When saving a new database in Access 2007-2016 databases, the file extension should be ________
A) .dbx B) .adbx C) .accdb D) .db