During the initial research for voice system security, who recognized that the most common security threats could be addressed by voice protection system?
a. The President's National Security Telecommunications Advisory Committee.
b. The Air Force Information Warfare Battle Lab.
c. The Air Force Network Integration Center.
d. The Cryptographic Systems Group.
Ans: b. The Air Force Information Warfare Battle Lab.
You might also like to view...
In the following code segment, what type of variable is counter?
``` Dim temp, counter, check As Integer Do temp = CInt(InputBox("Enter a number.")) counter += temp If counter = 10 Then check = 0 End If Loop Until (check = 0) ``` (A) counter (B) accumulator (C) sentinel (D) loop control variable
The properties in the Properties window can be sorted______________ or ______________ .
Fill in the blank(s) with the appropriate word(s).
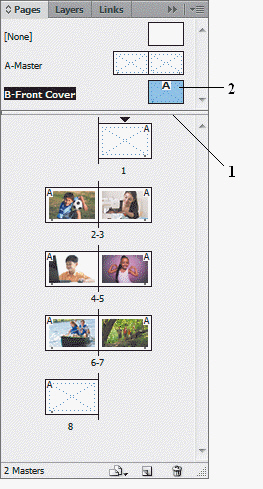 In the accompanying figure, the "A" in item 2 indicates that the A-Front Cover master page is based on the B-Master.
In the accompanying figure, the "A" in item 2 indicates that the A-Front Cover master page is based on the B-Master.
Answer the following statement true (T) or false (F)
Which power control option performs a warm boot?
a. Restart b. Sleep c. Log off d. Shut down