The security principle known as ________ gives individuals a certain level of access based on who they are.
A. authorization
B. validation
C. attenuation
D. authentication
Answer: A
You might also like to view...
Answer the following statements true (T) or false (F)
1. You can only use array indexed variables as arguments to methods. 2. A method can not change the values stored in the indexed variables of an array argument. 3. A collection class is a class whose objects store a collection of values. 4. You may cycle through elements of a collection object using a for loop. 5. In a vararg specification the ellipsis is not part of the Java syntax.
Which of the following is NOT checked by the Word Count feature in Word?
A) words B) objects C) pages D) paragraphs
The SUM function calculates the total of values contained in two or more cells
Indicate whether the statement is true or false
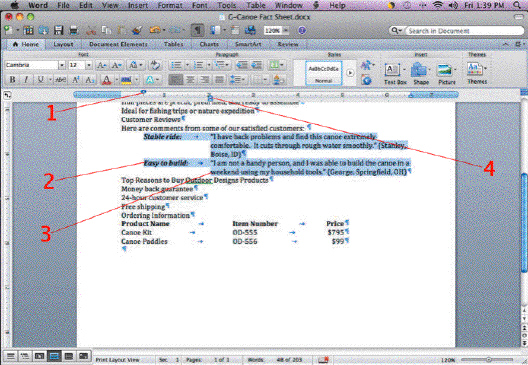 In the accompanying figure, Item 2 points to the first line of a paragraph that is ____ at the 1/2" mark.
In the accompanying figure, Item 2 points to the first line of a paragraph that is ____ at the 1/2" mark.
A. left-aligned B. right-aligned C. center-aligned D. justified