Content added using the:beforeand:afterpseudo-elements is known as __________ content.
A. generated
B. gradient
C. degraded
D. detected
Answer: A
You might also like to view...
The _________________, which is the latest of the RSA schemes, is the one that RSA Laboratories recommends as the most secure of the RSA schemes.
A. RSA-PSS B. ECDSA C. DSA-SDS D. EDSDS
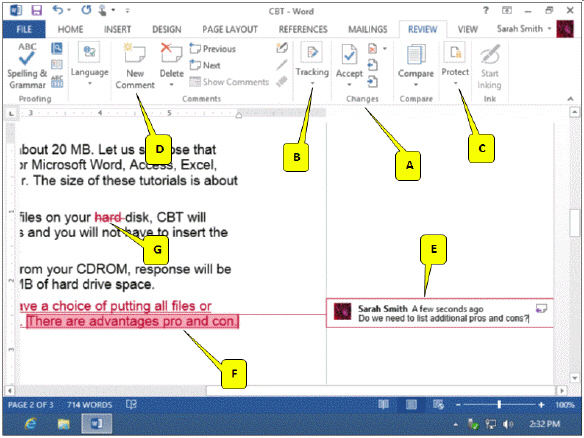 Refering to the accompanying figure, which of the following callouts points to the comment?
Refering to the accompanying figure, which of the following callouts points to the comment?
A. D B. G C. F D. E
Which of the following statements about quantitative risk analysis is true?
A. It is the most widely used approach to risk analysis. B. Probability data is not required for this type of risk analysis. C. It uses annual loss expectancy to rank events. D. It is reliable and accurate way to calculate risk.
The ____________________ tool offers you a method for quickly altering the width of a stroke by clicking and dragging on the stroke itself.
Fill in the blank(s) with the appropriate word(s).