Which of the following is considered a security benefit when utilizing virtualization?
A. Consolidating multiple OSs onto the same physical hardware.
B. Allowing multiple applications to be installed on physical machines.
C. Simulating a single operating system on multiple hardware platforms.
D. Isolating operating system when running multiple concurrent VMs.
Answer: D
You might also like to view...
IPSec ____ use a complex set of security protocols to protect information, including Internet Key Exchange (IKE), which provides for the exchange of security keys between the machines in the VPN.
A. endpoints B. access points C. tunnels D. concentrators
FIGURE 3-2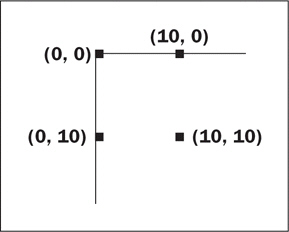 The Java coordinate system is oriented as shown in Figure 3-2 above.
The Java coordinate system is oriented as shown in Figure 3-2 above.
Answer the following statement true (T) or false (F)
import javax.swing.JOptionPane;public class Practice{ public static void main(String[] args) { String fullName; char firstLetter;________ }}Accepting a String from a user is common practice. Using the above code, write the statements to accept a String response from a user. Prompt the user with "Enter your name". Then use the charAt() method to extract the first character of the String.
What will be an ideal response?
You can ____________________ your folders and files to change the order they are listed.
Fill in the blank(s) with the appropriate word(s).