Provide steps to prepare the virtual environment.
Looking at logs is very important but it is also important to understand how network transactions hap-
pen at the packet level.
In this lab, you will analyze the traffic in a previously captured pcap file and extract an executable from
the file.
a. Launch Oracle VirtualBox. Right-click CyberOps Workstation > Settings > Network.
Beside Attached To, select Bridged Adapter, if necessary, and click OK.
b. Log in to the CyberOps Workstation VM (username: analyst / password: cyberops),
open a terminal, and run the configure_as_dhcp.sh script.
```
[analyst@secOps ~]$ sudo ./lab.support.files/scripts/configure_as_dhcp.sh
[sudo] password for analyst:
[analyst@secOps ~]$
```
You might also like to view...
Which of the following statements about image editing software is FALSE?
A) Free versions are not available. B) It can remove red eye. C) It can crop unwanted details. D) It can create photo montages.
FIGURE AC 2-1 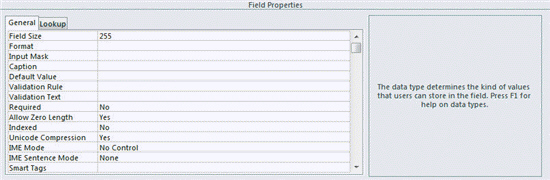 Figure AC 2-1 above, you would access this Field Properties screen in ____ view.
Figure AC 2-1 above, you would access this Field Properties screen in ____ view.
A. Datasheet B. Design C. Edit D. Table
EX Case 8-1Mr. Berry uses a worksheet to record grades for the math class he teaches two evenings a week at a local business college. Using Excel allows him to easily calculate the class averages and to use conditional formatting to analyze his students' grades. When choosing to use an icon set as conditional formatting, which of the following categories is NOT an option on the menu?
A. Directional B. Shapes C. Ratings D. Solid Fill
____ shows a correct array initialization statement.
A. char codes[6] = ['s', 'a', 'm', 'p', 'l', 'e']; B. char codes[] = ('s', 'a', 'm', 'p', 'l', 'e'); C. char codes[] = "sample"; D. char codes[*] = {'s', 'a', 'm', 'p', 'l', 'e'};