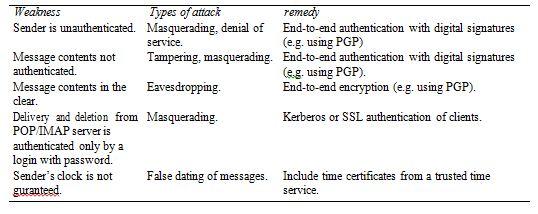
Describe some of the ways in which conventional email is vulnerable to eavesdropping, masquerading, tampering, replay, denial of service. Suggest methods by which email could be protected against each of these forms of attack.
What will be an ideal response?
Possible weaknesses for a typical mail system with SMTP delivery and client pickup from POP or IMAP mail host on a local network:
Computer Science & Information Technology
You might also like to view...
To see all open windows, you can display them side-by-side or ________ them
Fill in the blank(s) with correct word
Computer Science & Information Technology
Hyper-Threading allows a single processor to appear to the system as multiple processors
Indicate whether the statement is true or false
Computer Science & Information Technology
____ filters records that match multiple criteria using the same Access logical and comparison operators used in queries.
A. AutoFilter B. Filter by Selection C. Filter By Form D. Advanced Filter/Sort
Computer Science & Information Technology
What type of storage is used on mobile devices?
A. volatile memory B. ROM C. RAM D. flash memory
Computer Science & Information Technology