The concerns of privacy advocates were validated when it was revealed that the NSA had contracted with AT&T, Verizon, and BellSouth to collect information about ________ telephone calls
Fill in the blank(s) with the appropriate word(s).
Answer: domestic
You might also like to view...
In addition to ensuring adequate awareness of future risk, the risk management process also makes certain that a commonly accepted and systematic set of policies and procedures is in place to handle existing risks.
Answer the following statement true (T) or false (F)
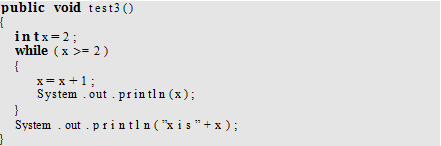
What will be output from the following code:
The ________ value causes a resource cost to be driven by the duration of the task multiplied by the hourly cost of the resource plus the cost per use charges if applicable.
Fill in the blank(s) with the appropriate word(s).
Which of the following is not a characteristic of a weak password?
A. Eight characters in length and include one or more uppercase letters, numbers, and symbols B. Uses default passwords such as password, admin, system, and guest C. Any sequence that includes a user name D. Use of a word from a dictionary