How does Linux protect user passwords from attackers, even if the attacker acquires the password file? How can this be circumvented?
What will be an ideal response?
Linux applies a hash algorithm to passwords before storing them in the password file.
If the attacker obtains the hash key, a dictionary attack can be used to obtain the password.
Password salting can reduce the risk of a successful dictionary attack.
You might also like to view...
The Java method printf is based on the ________ language.
a. Pascal b. C++ c. C d. ADA
After creating a gradient rectangle like the one in the accompanying figure, you can use the ____ Tool to select the rectangle and display its anchor points.
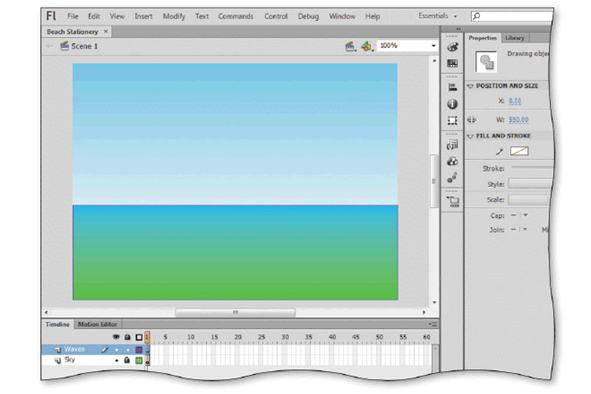
a. Subselection
b. Selection
c. Pen
d. Anchor
PSTN works with _______________ data.
Fill in the blank(s) with the appropriate word(s).
The printer subsystem that controls the movement of the paper through the printer is the _______ subsystem
A) Marking B) Print C) Paper transport D) Universal