A right tab stop aligns text with the right margin.
a. true
b. false
Answer: b. false
You might also like to view...
Consider the data set shown in Table 7.8. The first attribute is continuous, while the remaining two attributes are asymmetric binary. A rule is consid- ered to be strong if its support exceeds 15% and its confidence exceeds 60%. The data given in Table 7.8 supports the following two strong rules:
(i) {(1 ? A ? 2), B = 1}?{C = 1}
(ii) {(5 ? A ? 8), B = 1}?{C = 1}
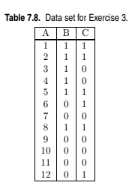
(a) Compute the support and confidence for both rules(b) To find the rules using the traditional Apriori algorithm, we need to
discretize the continuous attribute A. Suppose we apply the equal width
binning approach to discretize the data, with bin-width = 2, 3, 4. For
each bin-width, state whether the above two rules are discovered by
the Apriori algorithm. (Note that the rules may not be in the same
exact form as before because it may contain wider or narrower intervals
for A.) For each rule that corresponds to one of the above two rules,
compute its support and confidence.
(c) Comment on the effectiveness of using the equal width approach for
classifying the above data set. Is there a bin-width that allows you to find both rules satisfactorily? If not, what alternative approach can you
take to ensure that you will find both rules?
What are the differences between a standard USB flash drive and one protected with hardware encryption?
What will be an ideal response?
All GPOs are identified by their ________
a. Names b. Globally Unique Identifier (GUID) c. Fully Qualified Domain Names d. PolicyIDs
In general, a special journal would not be used to record
A. sales B. cash disbursements C. depreciation D. purchases