An attack that is using interference as its main attack to impede network traffic is which of the following?
A. Introducing too much data to a targets memory allocation
B. Utilizing a previously unknown security flaw against the target
C. Using a similar wireless configuration of a nearby network
D. Inundating a target system with SYN requests
Answer: C. Using a similar wireless configuration of a nearby network
You might also like to view...
Line-of-sight radio transmissions have an advantage of being able to go through tall land masses.
Answer the following statement true (T) or false (F)
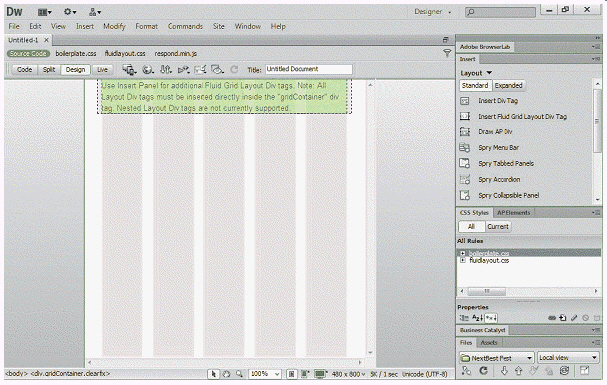 The accompanying figure shows the ____ grid page.
The accompanying figure shows the ____ grid page.
A. dynamic B. fluid C. structural D. indexed
In the following snippet of a Microsoft Excel 2016 worksheet, the information in cell B5 extends beyond the cell's border because:
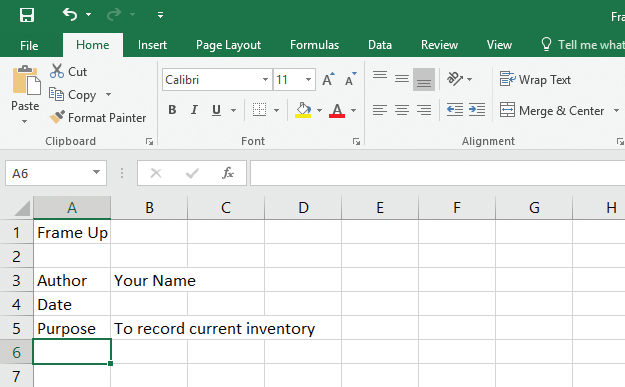
A. ?the cell borders have been removed. B. ?the text has been copied and pasted from a different cell. C. ?the cell next to it is empty. D. ?the format of row 5 allows text to spill over.
To create a web page using responsive design, you start by creating a layout that's optimized for both the smallest and the largest screen size you want to support.
Answer the following statement true (T) or false (F)