The __________ verifies a user’s right to access a computer and data.
a. operating system
b. compiler
c. interpreter
d. CPU
e. editor
a. operating system
You might also like to view...
Suppose an ArrayList list contains {"red", "red", "green"}. What is the list after the following code?
``` String element = "red"; for (int i = 0; i < list.size(); i++) if (list.get(i).equals(element)) list.remove(element); ``` a. {"red", "red", "green"} b. {"red", "green"} c. {"green"} d. {}
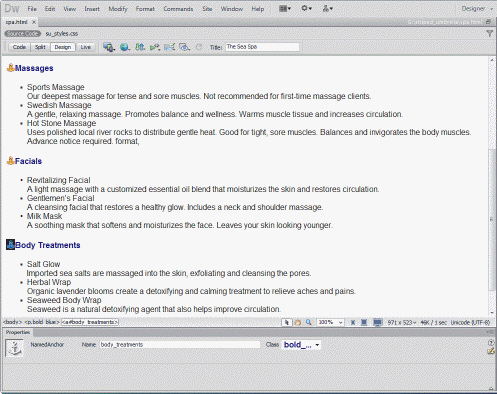 Named anchors, as shown in the accompanying figure, appear ____ when not selected.
Named anchors, as shown in the accompanying figure, appear ____ when not selected.
A. purple B. blue C. red D. yellow
What is a trigger inside of Unity?
What will be an ideal response?
Proper forensics procedures require _________ any evidence medium to make sure it’s not altered.
A. EBCDIC codes B. Write-protecting C. ... D. Investigator comments text box