Internet service providers use e-mail ____ techniques to verify that e-mail messages originate from the Internet domain from which they claim to have been sent.
A. firewall
B. authentication
C. concatenation
D. recovery
Answer: B
Computer Science & Information Technology
You might also like to view...
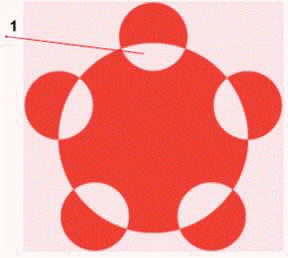 In the accompanying figure, item 1 points to one of the five positive spaces.
In the accompanying figure, item 1 points to one of the five positive spaces.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
________ is an assortment of tools that can be used to complete tasks like managing system performance
Fill in the blank(s) with correct word
Computer Science & Information Technology
File________ enables the user to reduce the number of bits in a file, which allows for faster transmission of the file
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The design of a help desk work area should reduce distractions, noise, and interruptions to the extent possible.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology