What command is used to verify that there is sufficient memory available to load a new version of the Cisco IOS software?
What will be an ideal response?
show flash
Computer Science & Information Technology
You might also like to view...
An RFID tag is commonly used for property security
Indicate whether the statement is true or false
Computer Science & Information Technology
You can use the ____ attribute within the
Computer Science & Information Technology
?
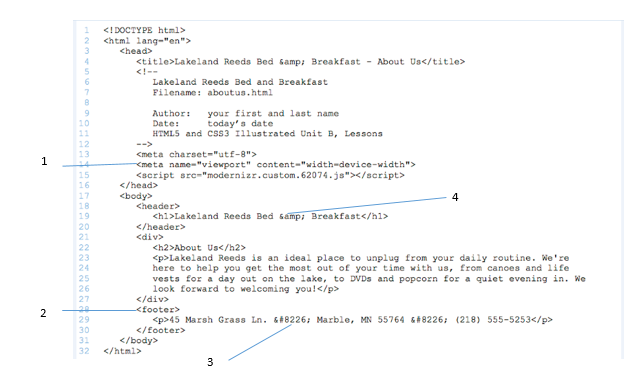
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
We are somewhat limited in our ability to protect which type of data?
A. Data in use B. Data at rest C. Data in motion
Computer Science & Information Technology