Summarize the different monitoring technologies and explain the importance of an employee monitoring policy.
What will be an ideal response?
Different monitoring technologies include (1) Key logger or key trapper software - records keystrokes and
mouse clicks, (2) Hardware key logger - capture keystrokes from the keyboard to the motherboard, (3)
Cookie - small file deposited on a hard drive by a Web site containing information about customers and
their Web activities, (4)Adware - generates self installing ads, (5) Spyware - hidden software that tracks
online movements, (6) Web log - consists of one line of information for every visitor to a Web site, (7)
Clickstream - records information about a customer during a Web surfing session. Employee monitoring
policies explicitly state how, when and where the company monitors its employees.
You might also like to view...
To avoid a confrontation with a customer and to avoid telling the customer he or she is wrong, a salesperson can use the head-on approach to handling objections
Indicate whether the statement is true or false
Customers today want separate prices for each service element, and they also want the right to select the elements they want. Customers are said to be pressing for ________ services
A) complementary B) perishable C) variable D) unbundled E) shared
Which of the following statements is TRUE?
Partial income statements of Company A and Company B are provided below:
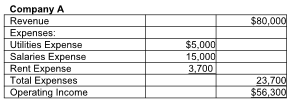
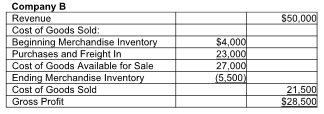
A) Company A is a merchandising company.
B) Company B is a manufacturing company.
C) Company A is a manufacturing company.
D) Company A is a service company.
A functional resume:
a. begins with a section on employment b. describes employment in chronological order c. describes employment in reverse chronological order d. none of the above