The __________ is unsuitable for a connectionless type of application because it requires the overhead of a handshake before any connectionless transmission, effectively negating the chief characteristic of a connectionless transaction.
A. timestamp approach
B. challenge-response approach
C. simple replay approach
D. one-way authentication approach
B. challenge-response approach
Computer Science & Information Technology
You might also like to view...
The ________________ reference always refers to the currently executing object.
a) null b) static c) final d) actual e) this
Computer Science & Information Technology
Find the number of spanning trees in the graph shown in Figure 2.5 in this document.
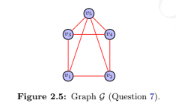
Computer Science & Information Technology
What is the best safeguard against zero-day attacks?
A. Enable auditing. B. Regularly inspect all logs. C. Update the hardware and software as soon as new updates are released. D. Implement backups.
Computer Science & Information Technology
The three components of a Premiere Products order are the heading, ____________________, and footing.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology