The Telnet protocol encrypts transmitted data, which therefore cannot be read by others on the network.
Answer the following statement true (T) or false (F)
False
Computer Science & Information Technology
You might also like to view...
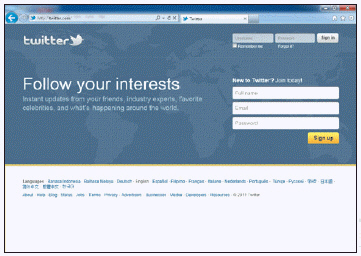 Which of the following activities is enabled by the resource shown in the accompanying figure?
Which of the following activities is enabled by the resource shown in the accompanying figure?
A. social networking B. cloud computing C. grid computing D. wiki usage
Computer Science & Information Technology
Inbound links increase the site's ranking in the search results of Google and other major search engines
Indicate whether the statement is true or false
Computer Science & Information Technology
A form that enables users to view but not change data is what type of form?
A) DataView B) DataView-only C) Read-only D) Restrict-only
Computer Science & Information Technology
Numbered lists that are separated by other text or objects can be formatted to display ________ numbering
A) increased B) decreased C) continuous D) restored
Computer Science & Information Technology