Effective management of information security is NOT an ongoing process; updates should be made periodically.
a. true
b. false
Answer: b. false
Computer Science & Information Technology
You might also like to view...
A function includes the function ____, which identifies it.
A. name B. parameter C. term D. id
Computer Science & Information Technology
Travelocity's application requests data from Weather Underground by calling its Web service through its ____.
A. XML B. plug-in C. API D. script
Computer Science & Information Technology
FIGURE 14-1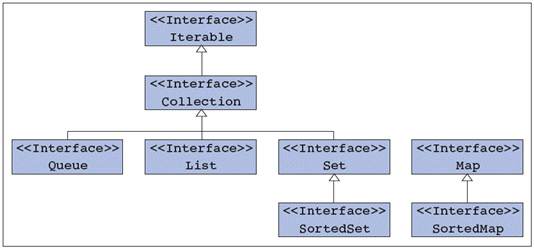 In Figure 14-1 above, the Collection interface extends the ____ interface.
In Figure 14-1 above, the Collection interface extends the ____ interface.
A. list B. set C. Iterable D. both a. and b.
Computer Science & Information Technology
Because tables often have more rows than can fit on a page, you can define the first row of a table as the print ____________________, which prints at the top of every page.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology