The ________ dialog box is common to most Office applications
A) Discover and Modify B) Find and Replace
C) Locate and Change D) Seek and Substitute
B
You might also like to view...
Provide at least five different suggestions for how to protect your privacy online.
What will be an ideal response?
Consider the following database schema, where the keys are underlined:
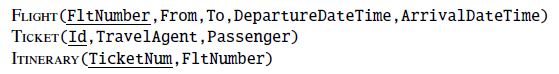
(a) Use both the relational algebra and SQL to answer the following query:
Find all possible trips from LA to NYC, which consist of two connecting flights.
(Flights connect if flight 1 arrives at the airport from where flight 2 leaves and
the arrival time of flight 1 is less than the departure time of flight 2. You can
use < to compare the times.)
(b) Use relational algebra only to answer the following query:
Find the travel agents who issued a ticket for 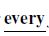 flight originating in LA.
flight originating in LA.
(c) Use SQL for the following query:
Find the travel agents who sold more than 5 tickets.
(d) Use SQL (only) to
Find the travel agents who sold the most number of tickets (among all the
agents).
What is the best way to protect against data loss on a stolen Windows 7 business laptop?
A) Use a USS. B) Use a biometric device. C) Use three-way authentication. D) Use BitLocker.
____________________ access calls for using a unique physical characteristic of a person to permit access to a controlled IT resource.
Fill in the blank(s) with the appropriate word(s).