Evaluate the expression, being careful to follow the order of operations. 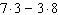
A. ![]()
B. ![]()
C. ![]()
D. ![]()
E. ![]()
Answer: A
You might also like to view...
All that is needed for an inline style is a property and a value
Indicate whether the statement is true or false
How does the Photomerge Scene Cleaner work?
What will be an ideal response?
Your network has been segmented into the following security zones. Zone 1 connects to the Internet through a router. Zone 2 is a closed research and development network. Zone 3 contains an intermediary switch supporting a SAN, dedicated to long-term audit log and file storage. Zone 4 contains a DMZ with an email server The company has budgeted for a single patch server. To which zone should this
limited resource be deployed? A. Zone 1 B. Zone 2 C. Zone 3 D. Zone 4
Which type of attack is a form of social engineering?
A. Denial of Service B. Smurf attack C. Phishing D. Zombie