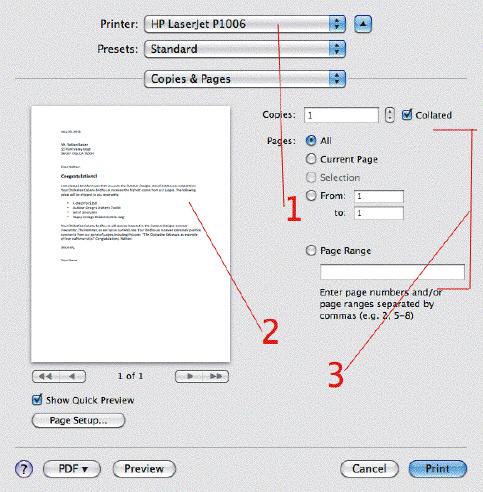
 In the accompanying figure, Item 1 tells you whether the ____.
In the accompanying figure, Item 1 tells you whether the ____.
A. printer is out of paper
B. correct printer is selected
C. printer is offline
D. correct document is selected
Answer: B
You might also like to view...
What access control model below is considered to be the most restrictive access control model, and involves assigning access controls to users strictly according to the custodian?
A. Mandatory Access Control B. Role Based Access Control C. Discretionary Access Control D. Rule Based Access Control
When a method resides entirely within another method, and can only be called from within the containing method, what is the method known as?
A. It is a local function. B. It is a client function. C. It is a parent function. D. It is a scope function.
The Institute of Electrical and Electronics Engineers (IEEE) has established worldwide networking protocols, including the Open Systems Interconnection (OSI) reference model.
Answer the following statement true (T) or false (F)
Describe how a string is a reference and how a string comparison is done.
What will be an ideal response?