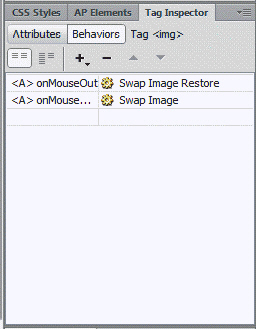
 An event like the one in the accompanying figure has two components: the user event and the ____________________.
An event like the one in the accompanying figure has two components: the user event and the ____________________.
Fill in the blank(s) with the appropriate word(s).
event handler
You might also like to view...
Answer the following statements true (T) or false (F)
1. Each byte is assigned a unique number known as an address. 2. Encapsulation refers to the combining of data and code into a single object. 3. Java source files end with the .class extension. 4. A procedure is a set of programming language statements that, together, perform a specific task. 5. A solid-state drive has no moving parts and operates faster than a traditional disk drive.
What can go wrong if every user of a Linux system has unlimited access to resources?
What will be an ideal response?
________ uses a password to create a unique algorithm used to translate the saved Excel workbook into a stream of uninterpretable characters that can only be translated back with that password
Fill in the blank(s) with correct word
Which of the following would be the result if you placed *thin your criteria?
a. mathematics b. straight c. three d. math