A network technician has discovered a rogue access point placed under an empty cubicle desk. Witch of the following should the technician partners ensure another cannot be placed on the network?
A. Disable unused ports on switches.
B. Enable DHCP guard to detect rogue servers.
C. Configure WPA2 on all access points.
D. Use TACACS+ authentication.
Answer: B. Enable DHCP guard to detect rogue servers.
Computer Science & Information Technology
You might also like to view...
Explain the role of the CISO.
What will be an ideal response?
Computer Science & Information Technology
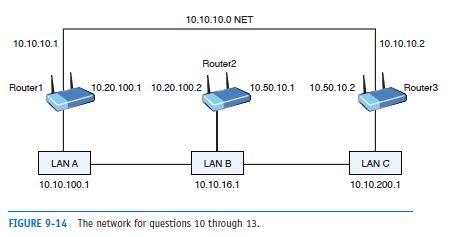
List two static routes to route data from LAN B to LAN C in the network shown in Figure 9-14, assuming the subnet mask 255.255.255.0.
Figure 9-14
Computer Science & Information Technology
A printer that is connected correctly, turned on, and available for operation is:
A) offline. B) linked. C) direct. D) online.
Computer Science & Information Technology
The text you add to a SmartArt graphic can serve as keywords, or a speaking outline._________________________
Answer the following statement true (T) or false (F)
Computer Science & Information Technology