Identity theft and mistaken identity are the same.
Answer the following statement true (T) or false (F)
False
You might also like to view...
The strategy of resource allocation denial is referred to as the ___________
Fill in the blank(s) with the appropriate word(s).
A good rule of thumb is to design your website so that viewers are never more than ____ clicks away from the page they are seeking.
A. one or two B. two or three C. five or six D. seven or eight
Find the error in each of the following program segments and correct the error:
a) #include
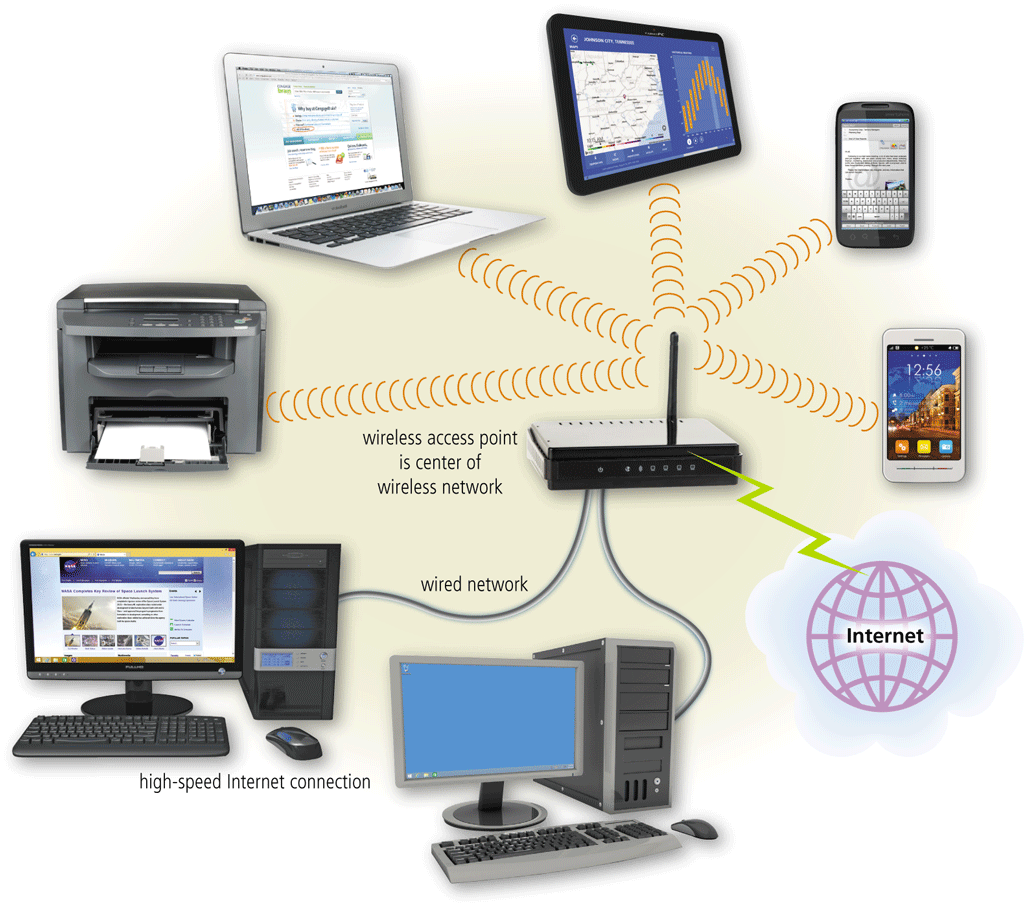
A. P2P B. SLAN C. WLAN D. FTP