Consider the relational schema in Figure 3.6. Assume that the Web server delivers the contents of these relations using the following XML format: the name of the relation is the top-level element, each tuple is represented as a tuple element, and each relation attribute is represented as an empty element that has a value attribute. For instance, the Student relation would be represented as
follows:
Formulate the following queries using XQuery:
a. Produce the list of all students who live on Main Street.
b. Find every course whose CrsCode value does not match the Id of the department that o?ers the course. (For instance, the course IS315 in information systems might be o?ered by the Computer Science (CS) Department.)
c. Create a list of all records from the Teaching relation that correspond to courses taught in the fall semester.
a.
{
FOR $s IN doc("http://xyz.edu/student.xml")//tuple
WHERE contains($s/Address/@value,"Main St")
RETURN $s
}
b.
{
FOR $c IN doc("http://xyz.edu/course.xml")//tuple
WHERE NOT contains($c/CrsCode/@value,$c/DeptId/@value)
RETURN $c
}
c.
{
FOR $t IN doc("http://xyz.edu/teaching.xml")//tuple
WHERE starts-with($t/Semester/@value,"F")
RETURN $t
}
You might also like to view...
Is the ________ tool
Fill in the blank(s) with correct word
FIGURE WD 4-1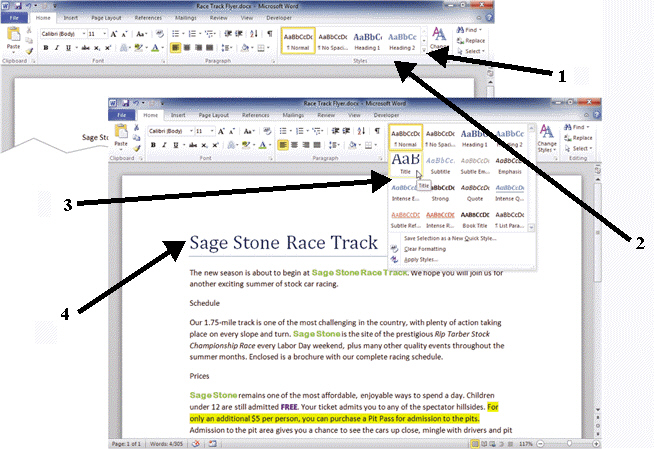 The item numbered 4 in Figure WD 4-1 above is the ____ of the Title Quick Style.
The item numbered 4 in Figure WD 4-1 above is the ____ of the Title Quick Style.
A. Live Preview B. Final Result C. Quick View D. Font View
All security experts recommend disconnecting from the computer network before opening email attachments.
Answer the following statement true (T) or false (F)
An IDS is used for which of the following purpose?
A. Controls inbound and outbound connections to prevent unauthorized access to the Internet. B. Controls inbound and outbound connections in a network device by command lines. C. Monitors inbound and outbound network connections in order to identify suspicious activity. D. Monitors inbound and outbound network connections in order to prevent suspicious activity