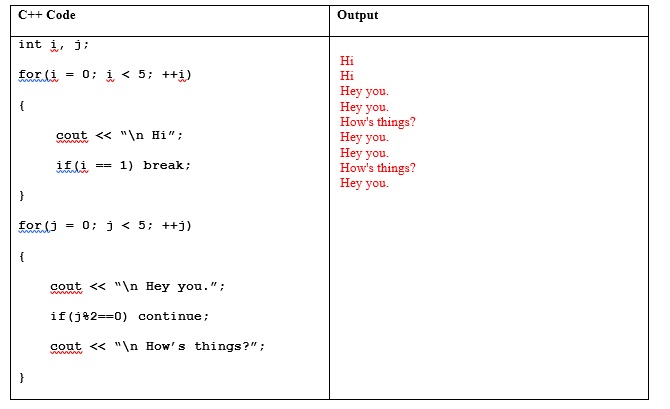
What will be the output from the source code?

Computer Science & Information Technology
You might also like to view...
In Microsoft Internet Explorer, Web pages that users wish to return to in the future are called ________
Fill in the blank(s) with correct word
Computer Science & Information Technology
Which of the following would BEST meet a server authentication requirement for a wireless network, but the network has no PKI in place?
A. PEAP B. PAP C. EAP-TLS D. LEAP
Computer Science & Information Technology
Briefly distinguish between scheduled and unscheduled programs.
What will be an ideal response?
Computer Science & Information Technology
Explain vendor exploitation.
What will be an ideal response?
Computer Science & Information Technology