During an investigation, a security analyst determines suspicious activity occurred during the night shift over the weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website. Which of the following would be the MOST appropriate recommendation to prevent he activity from happening in the future?
A. An IPS signature modification for the specific IP addresses
B. An IDS signature modification for the specific IP addresses
C. A firewall rule that will block port 80 traffic
D. A firewall rule that will block traffic from the specific IP address
Answer: D. A firewall rule that will block traffic from the specific IP address
You might also like to view...
The command to restore (yank) the killed section of the text is:
a: [Alt-y] b: [Alt-x][Ctrl-y] c: [Ctrl-yank] d: [Ctrl-y] e: [Ctrl-x] y
If an Excel printout extends to more than one page, add ________ to the header or footer
A) the file name B) a page number C) the date D) the user's name
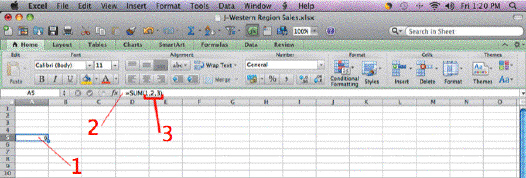 In the accompanying figure, Item 2 points to the ____.
In the accompanying figure, Item 2 points to the ____.
A. formula in the function bar B. function in the formula bar C. SUM in the status bar D. cell reference
As you type an e-mail message, Outlook automatically corrects some misspelled words.
Answer the following statement true (T) or false (F)