In the AES structure both encryption and decryption ciphers begin with a(n) __________ stage, followed by nine rounds that each include all four stages, followed by a tenth round of three stages.
A. Substitute bytes
B. AddRoundKey
C. MixColumns
D. ShiftRows
B. AddRoundKey
You might also like to view...
Which of the following is a multi-alphabet cipher?
A) Caesar cipher B) ROT13 C) At bash cipher D) Vigenère
Match the following acronyms to their functions:
I. C2C II. POD III. B2B IV. B2C V. e-commerce A. businesses buying and selling with each other B. the ability to print a few books at any time C. individuals setting up a Web page to buy and sell products with each other D. made possible by secure communications E. businesses selling directly to the consumer
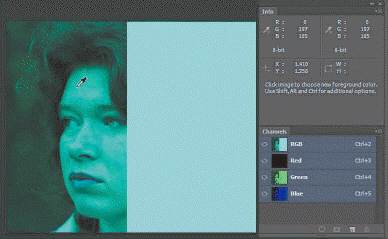 In the accompanying figure, based on the INFO tab, the image can be described as ____.
In the accompanying figure, based on the INFO tab, the image can be described as ____.
A. Cyan = Minus Red B. Cyan = Minus Green C. Yellow = Minus Blue D. Yellow = Minus Red
Group Policy can be linked to at a user level
a. true b. false