Employees' last names would usually make an appropriate primary-key field
Indicate whether the statement is true or false
FALSE
Computer Science & Information Technology
You might also like to view...
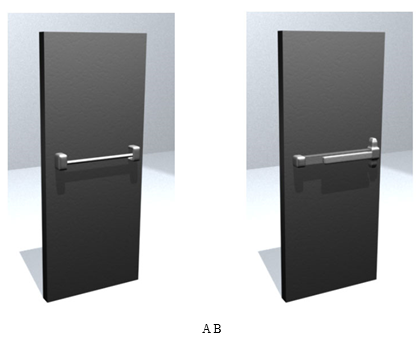
The following are pictures of two doors. How would you operate door A? How would you operate door B? Compare the your answers to these questions and explain the reasons for your conclusions.
Computer Science & Information Technology
The use of ____ is required to achieve RSN compliance.
A. WPA2 B. CCMP C. TKIP D. EAP
Computer Science & Information Technology
____ is the predominant cryptographic authentication and encryption protocol suite in use today.
A. Secure Hypertext Transfer Protocol (SHTTP) B. Public key infrastructure (PKI) C. Privacy Enhanced Mail (PEM) D. IP Security (IPSec)
Computer Science & Information Technology
What memory feature enables the BIOS/UEFI to determine exact details about the memory module?
A) VCM B) STD C) ECC D) SPD
Computer Science & Information Technology