Graph the point. 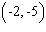
A. 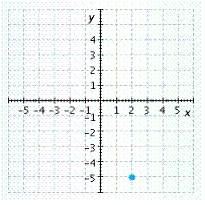
B. 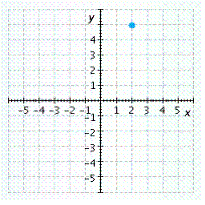
C. 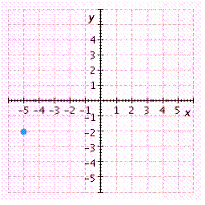
D. 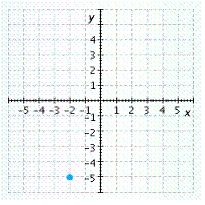
E. 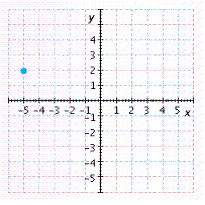
Answer: D
You might also like to view...
The ____ is primarily responsible for ensuring that configuration management practices are effective, and that security controls built into the process identify and mitigate any vulnerabilities induced during the lifecycle of the system.
A. IT security compliance officer B. IT security of operations professional C. digital forensics professional D. IT risk professional
A pull quote is a phrase or sentence taken from an article to emphasize a key point, which may be in larger type, a different font, or italics
Indicate whether the statement is true or false
You require a protocol in order for your Windows network hosts to have access to shared files and folders. Which of the following protocols will provide the necessary file services? (Select TWO.)
A. CIFS B. SNMP C. SMTP D. SLP E. RDP F. SMB
Which type of cabling does the 10BaseTstandard specify?
A. Coaxial B. Shielded Twisted Pair (STP) C. Fiber-Optic D. Unshielded Twisted Pair (UTP)