When malicious code is planted on your computer and alters your browser's ability to find web addresses, it is known as ________.
A. phishing
B. pharming
C. pretexting
D. polymorphing
Answer: B
You might also like to view...
Write function distance, which calculates the distance between two points (x1, y1) and (x2, y2). All numbers and return values should be floating-point values. Incorporate this function into a script that enables the user to enter the coordinates of the points through an HTML form.
What will be an ideal response?
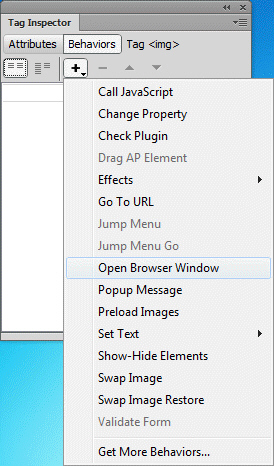 The list of available commands shown in the accompanying figure is the ____.
The list of available commands shown in the accompanying figure is the ____.
A. Behaviors menu B. Actions menu C. Event drop down list D. Special Effects drop down list
____ is the system administrator login in SQL Server and it holds great power on the database.
A. BUILT-IN\Administration B. Admin C. SYS D. SA
In order to use a variable both with a try or catch block and afterward, you must declare the variable before the ____ block begins.
A. catch B. try C. main D. finally