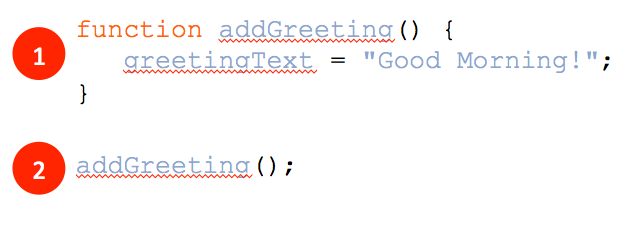
Referring to the figure above, which of the following is a function name used in the code shown?
A. greetingText
B. addGreeting
C. Good Morning!
D. function
Answer: B
You might also like to view...
IPSec ____ use a complex set of security protocols to protect information, including Internet Key Exchange (IKE), which provides for the exchange of security keys between the machines in the VPN.
A. endpoints B. access points C. tunnels D. concentrators
What are the benefits of using UDP instead of TCP as a transport protocol for DNS?
What will be an ideal response?
Critical Thinking QuestionsCase D-2Beth is running for student council, and she is in the middle of creating her campaign poster. She is using Photoshop because of the various ways it allows her to add effects to type. Beth wants to fill her type with something eye-catching. Which of the following options does she have?
A. drop shadow and gradient B. gradient and imagery C. emboss and drop shadow D. color and glow
When you use computing resources of another computer over a network, you are using ________
Fill in the blank(s) with the appropriate word(s).