Describe with examples how legal frameworks in place to support transnational management of data can prove ineffective in protecting the privacy or business or consumers.
What will be an ideal response?
This project requires that students gather information through research to identify the issues that
governments and organizations face to protect their data that is store, processed and moved
between countries and is therefore subject to different and sometime conflicting jurisdictions.
You might also like to view...
Answer the following statements true (T) or false (F)
1. Access to high-speed communication lines (such as cable) calls for a cable modem. 2. Some peripheral devices are linked directly to the processor. 3. A buffer is temporary memory or storage used to adjust for the speed differential between the processor and memory. 4. Certain functions (for example, deciding where the next byte can be found or stored in memory and counting the characters transferred to or from an external device) are common to almost all types of input and output. On larger machines, they are performed by each interface; in effect, they are duplicated for each device on the system. 5. On a mainframe computer, a channel handles device-independent functions and device- dependent functions are implemented through I/O control units or interface units.
In which type of attack do attackers intercept the transmissions of two communicating nodes without the user's knowledge?
A. rogue device B. wardriver C. man-in-the-middle D. brute force
?Identify the letter of the choice that best matches the phrase or definition.
A. ?It identifies the report and contains the report title, date, and other necessary information. B. ?When you reduce this, you avoid unnecessary labor costs, get data into the system more quickly, and decrease the number of errors. C. ?It is especially important in designing large-scale systems because separate teams of analysts and programmers can work on different areas and then integrate the results. D. ?It produces an early, rapidly constructed working version of a proposed information system. E. ?It can include grand totals for numeric fields and other end-of-report information. F. ?They are generally paper-based but can be provided online. G. ?This explains what is required on a form if variable input data is needed. H. ?It is a starting point with well-placed command buttons that allow users to navigate the system. I. ?It is a type of report that is useful when the user wants information only on records that might require action. J. ?It is a type of check that is used for mandatory data items.
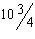 Item D in the accompanying figure is used to do which of the following?
Item D in the accompanying figure is used to do which of the following?
A. Lock the Scale values B. Update changes to the Scale values C. Constrain the Scale values D. Set default Scale values